Apps are at the heart of modern businesses, and are important assets that need a secure platform geared for compliance and security. We launched Heroku Enterprise earlier this year with this in mind and today we are excited to announce the beta of Heroku Identity Federation for Heroku Enterprise customers. This feature unifies the login experience across Salesforce's new App Cloud that we announced today.
As customers like Forever Living, TV4 and Macy’s run more of their apps and business-critical services on Heroku, they need tighter integration with their existing security infrastructure. With our new identity federation feature, customers can confidently meet compliance mandates such as password complexity requirements, rotation policies, access restrictions and onboarding / offboarding procedures, without having to re-implement them on Heroku.
Introducing Heroku Identity Federation
Heroku Identity Federation allows access to a Heroku organization to be managed through a third party identity provider (IdP) such as Salesforce Identity or Microsoft Active Directory. Many organizations already use such systems for managing employee access to business systems.
Once you set up an organization for identity federation, users logging into the organization are redirected to the identity provider for authentication. After a successful login with the IdP, they are directed back to the Heroku Dashboard for the organization. When a user successfully logs in for the first time through this flow, they are added as members to the org. As members, they can view existing apps and create new apps. They can also be granted more privileges on specific apps.
Setting up an organization for Identity Federation
For the beta, we are enabling SAML based integration, which will allow you to configure an organization for identity federation with various SAML compliant identity management products, such as Salesforce Identity and Microsoft Active Directory Federation Services.
Heroku organization admins can configure identity federation in the Settings page of the organization in the Heroku Dashboard. Please see the Setting up your Heroku Enterprise organization for identity federation Dev Center article for more details.
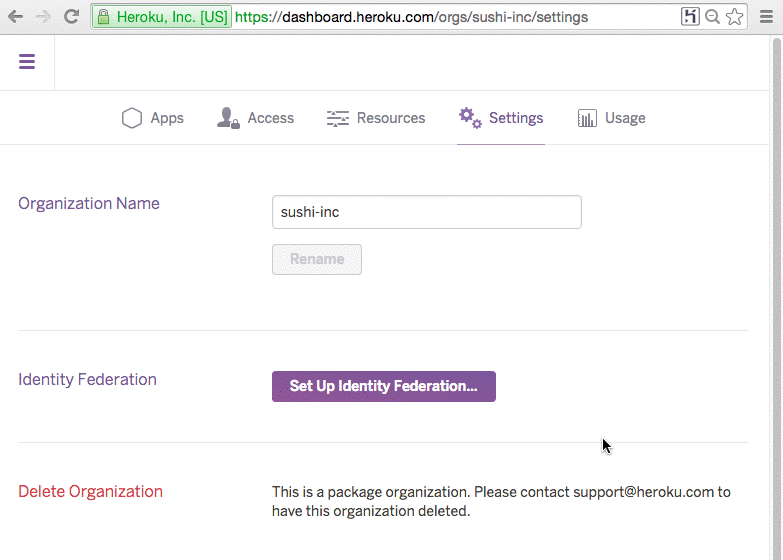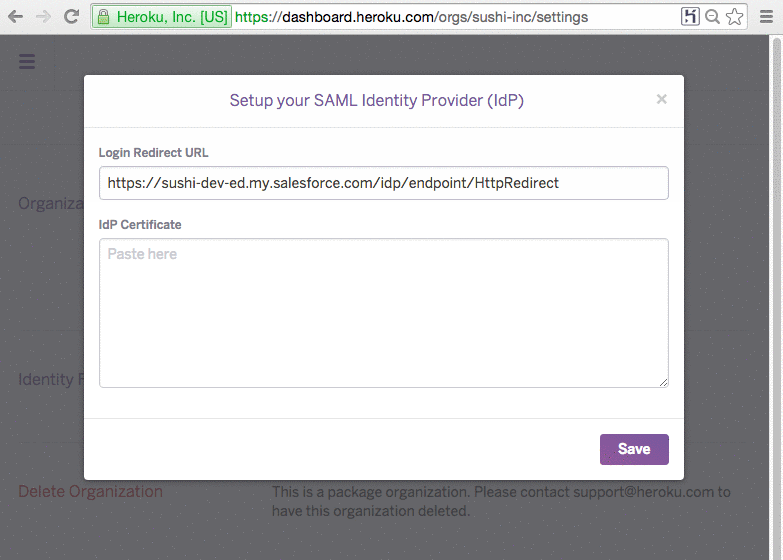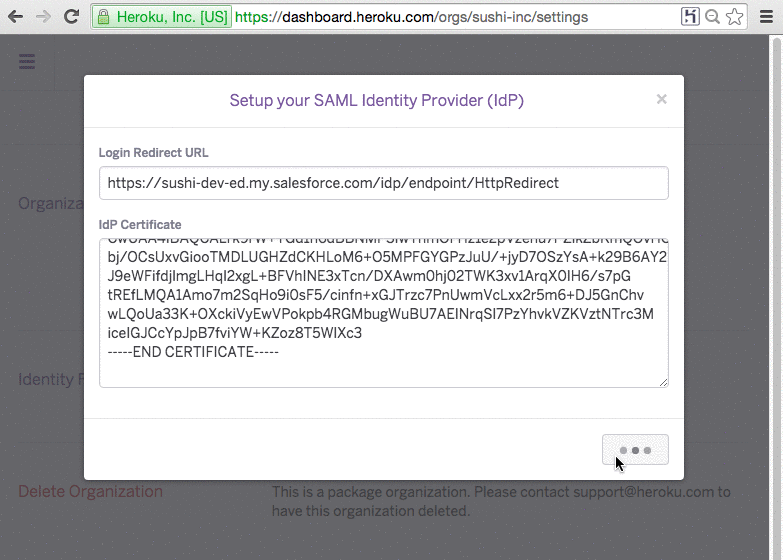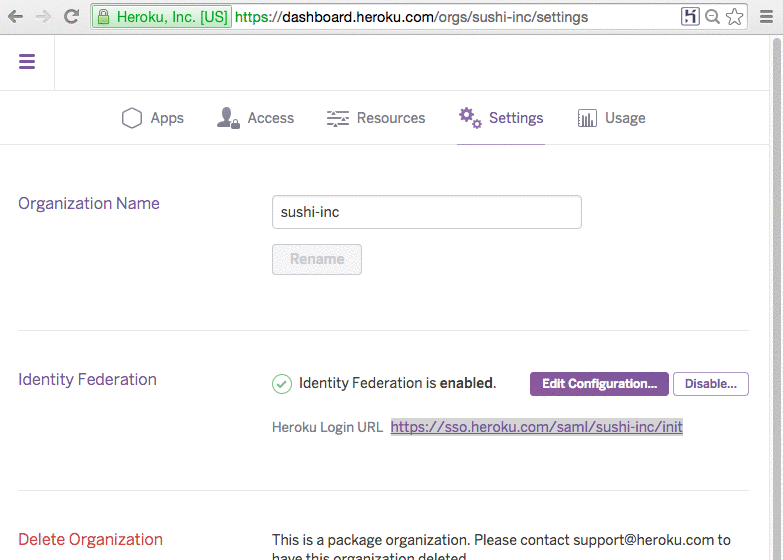
Once configuration is complete, identity federation is enabled and a Heroku Login URL that is unique to your organization is shown in the Settings page. You can email it to all users that you want to allow access to the organization or place it in a shared location such as a single sign-on (SSO) portal or an intranet webpage.
Logging into a federated organization
Users login to a identity federated organization by navigating to the org specific URL such as https://sso.heroku.com/saml/sushi-inc/init. They are redirected to the identity provider and on successful authentication redirected back to the Heroku Dashboard page for the org. Once a user is logged in, they are granted a token that gives them access to the organization and the apps in it. This token expires every 8 hours after which users will have to re-authenticate with the identity provider.
Users can also continue to use the Heroku CLI as they normally would. When they log in for single sign-on through the CLI, a browser instance is fired up allowing them to authenticate with the identity provider. On successful authentication, they are presented with an access token that they can use to configure their CLI session.
Onboarding and offboarding
When new employees join, they are typically provisioned an user record in the identity provider, and can then log into the Heroku organization through the org specific login URL. An org admin can also immediately add them as a member which sends them the unique URL for the org in an invite email.
Administrators often prefer a centralized mechanism to revoke a user’s access to business systems when the user leaves the company. When an employee is removed from the identity provider, they can no longer log into the Heroku organization. If they are already logged in, any tokens that they have been issued will expire within 8 hours after which they will no longer be able to access the organization or its apps. You can also immediately remove them by calling this API.
Managing users
Once an organization is set up for identity federation, admins no longer have to add users. Anybody who has access to the Heroku login URL and can successfully authenticate with the identity provider will automatically be added a member on their first login. Existing members can log in using their Heroku username and password. The first time they log in through the IdP, they are converted to a federated user and subsequently can login only through the IdP.

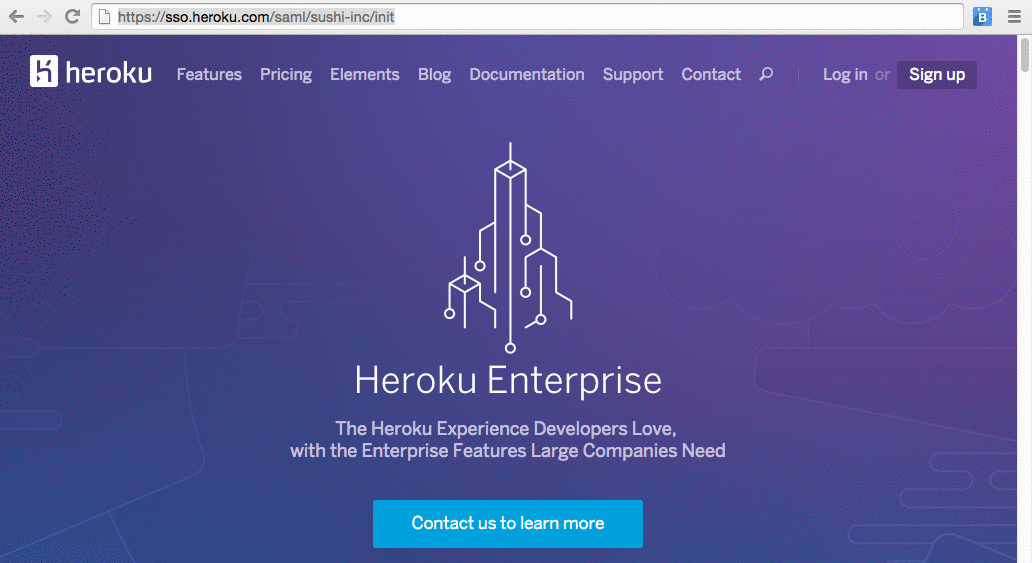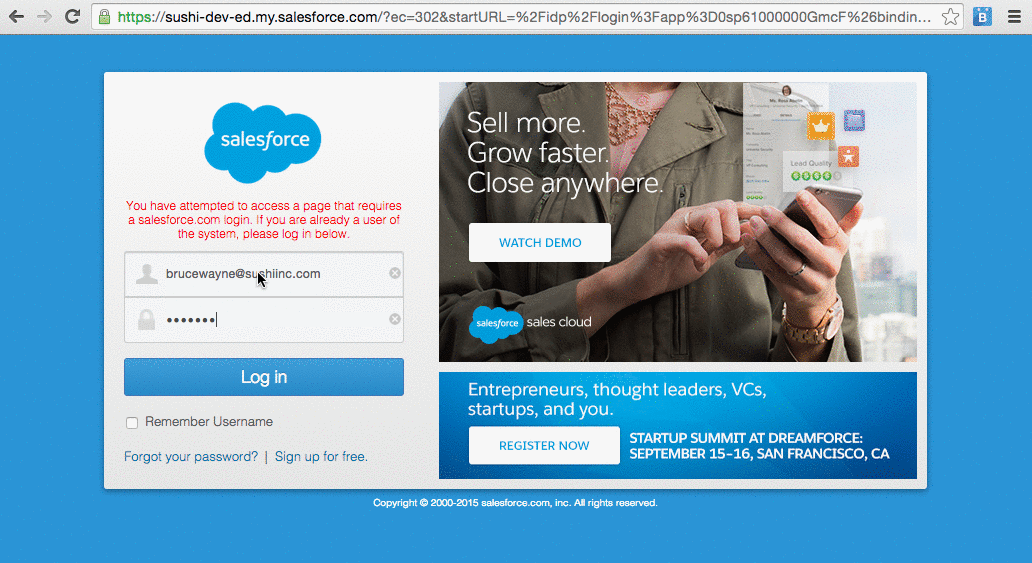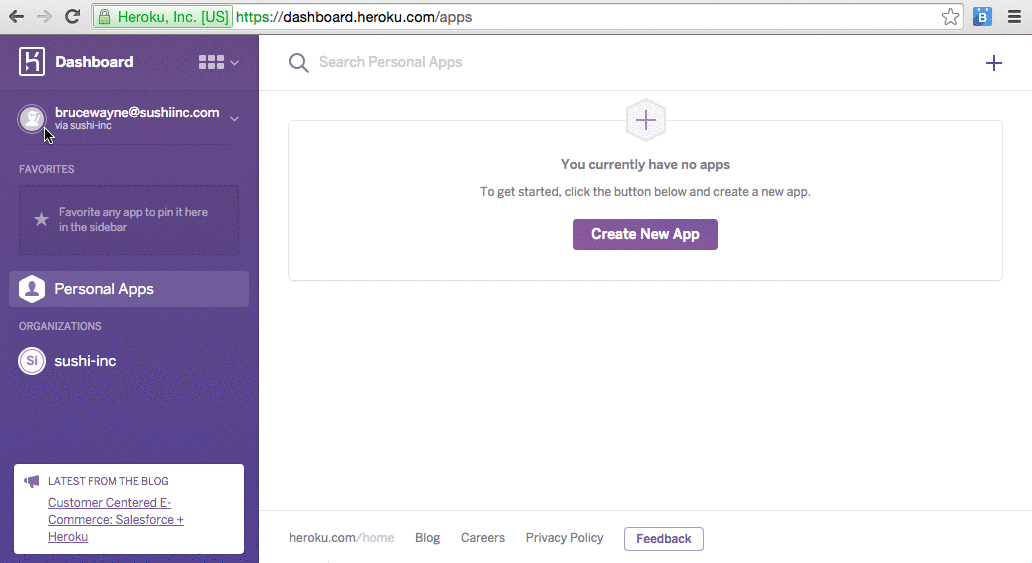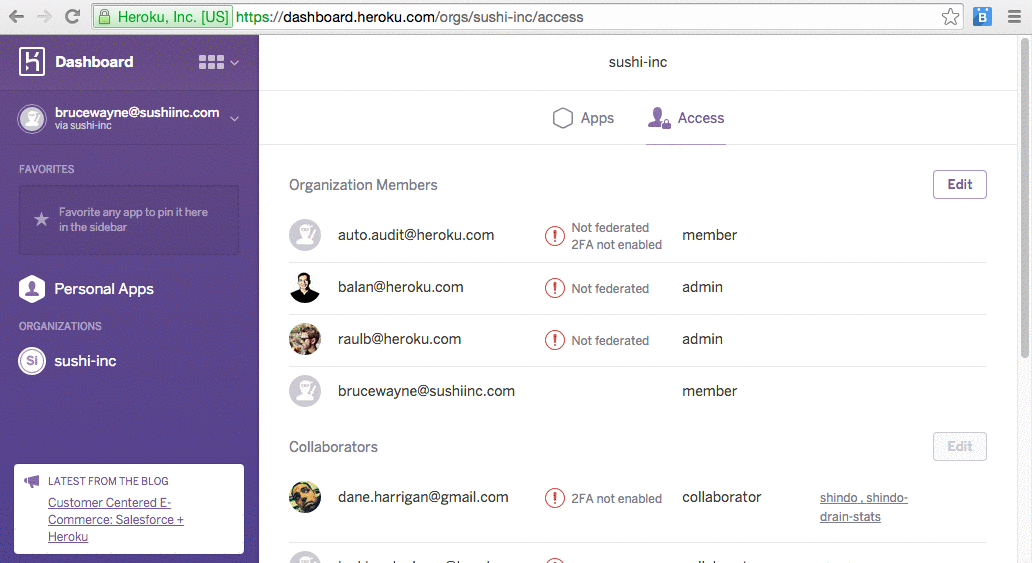
Organization members that use a Heroku username and password are highlighted as 'Not federated' in the organization access page, enabling you to quickly scan for members that don't use SSO. You can also see the 2FA status of such users in the org access page. If you want to allow access only through your identity provider, you can remove all such non-federated users from the org. On the other hand, you can also allow some users who may not be able to log in through the identity provider, such as contractors, to access the organization (or specific apps) using their Heroku username and password.
Next steps
We are very excited about bringing identity federation to our customers as a beta feature of Heroku Enterprise. Please sign up for the beta and we will be in touch shortly. For feedback and questions, contact us at enterprise-feedback@heroku.com.